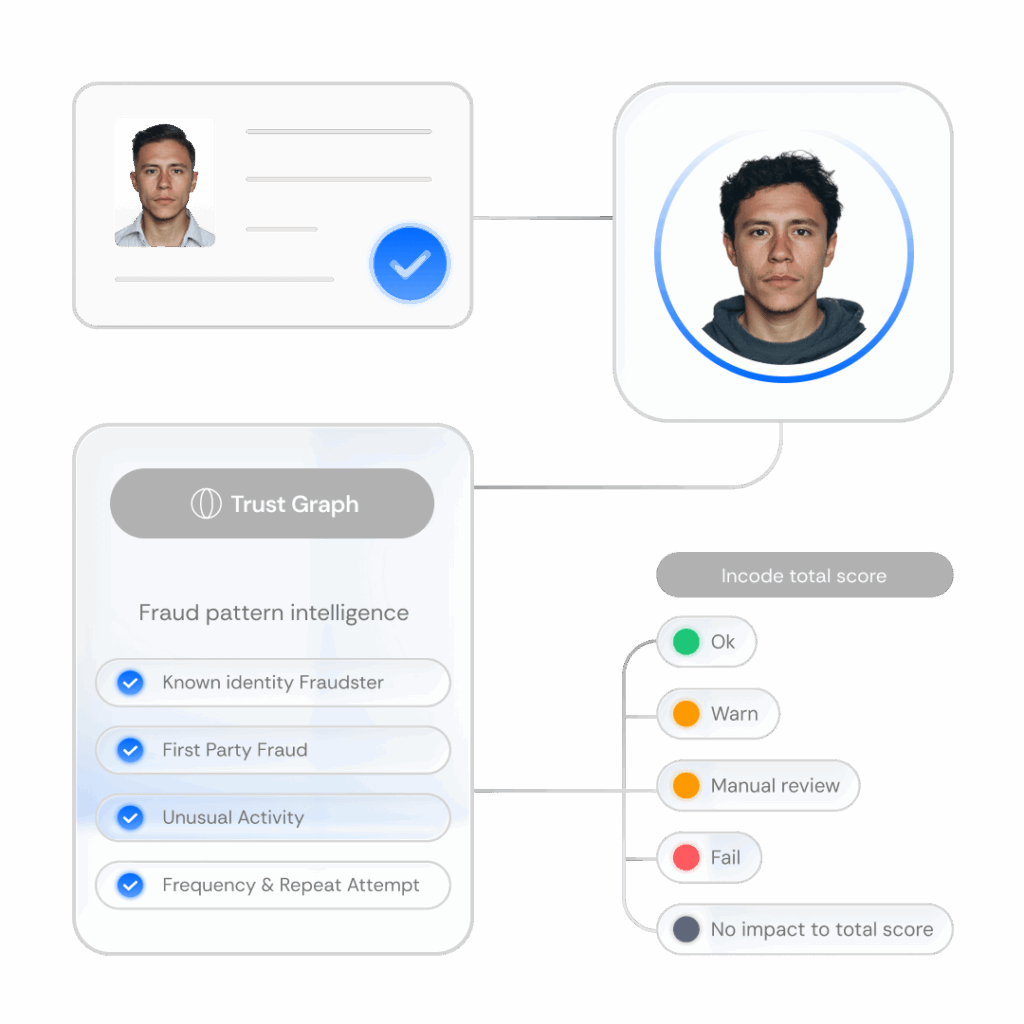
Trust Graph
Detect and block repeat attackers
Trust Graph detects duplicate, synthetic, and reused identities across sessions and organizations, without ever exposing PII.
Trusted by the world’s leading companies

Our technology
How Trust Graph protects your business
By maximizing a collective defense to flag patterns like duplicate users, reused documents, and synthetic identities, Trust Graph delivers shared threat intelligence and synthetic identities without exposing any PII.

Block repeat fraudsters
By connecting risk signals across a global network, Trust Graph delivers earlier detection with greater precision. That means stopping more fraud without adding friction for trusted users.

Strengthen defense with collective intelligence
Contribute internal signals to Trust Graph to strengthen the network and gain real-time insight into threats flagged elsewhere.
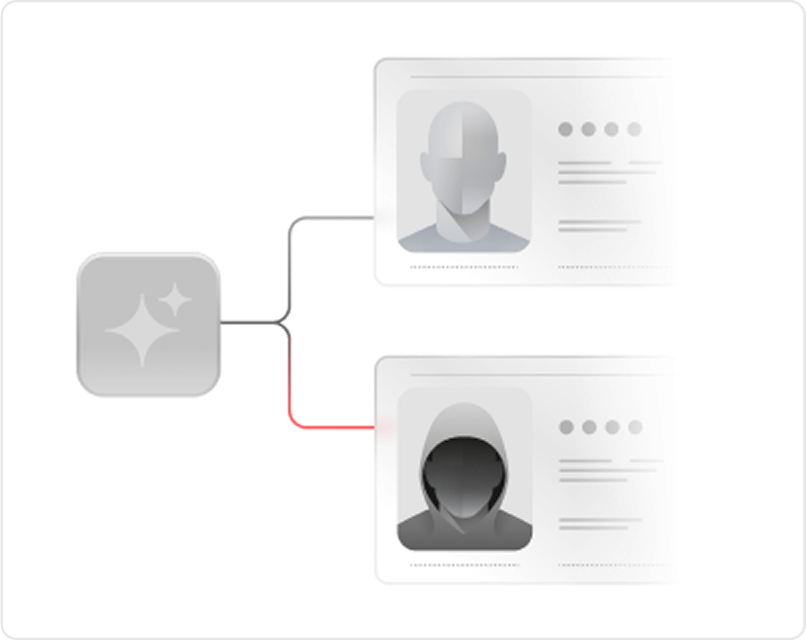
Security without compromise
Trust Graph protects user data while delivering high-impact results. All risk signals are anonymized to meet the strictest data security and privacy standards.
The Incode Difference
Trusted signals sourced across the network
Move beyond isolated, reactive fraud prevention. Collective risk signals work together to proactively stop threats before they become losses.
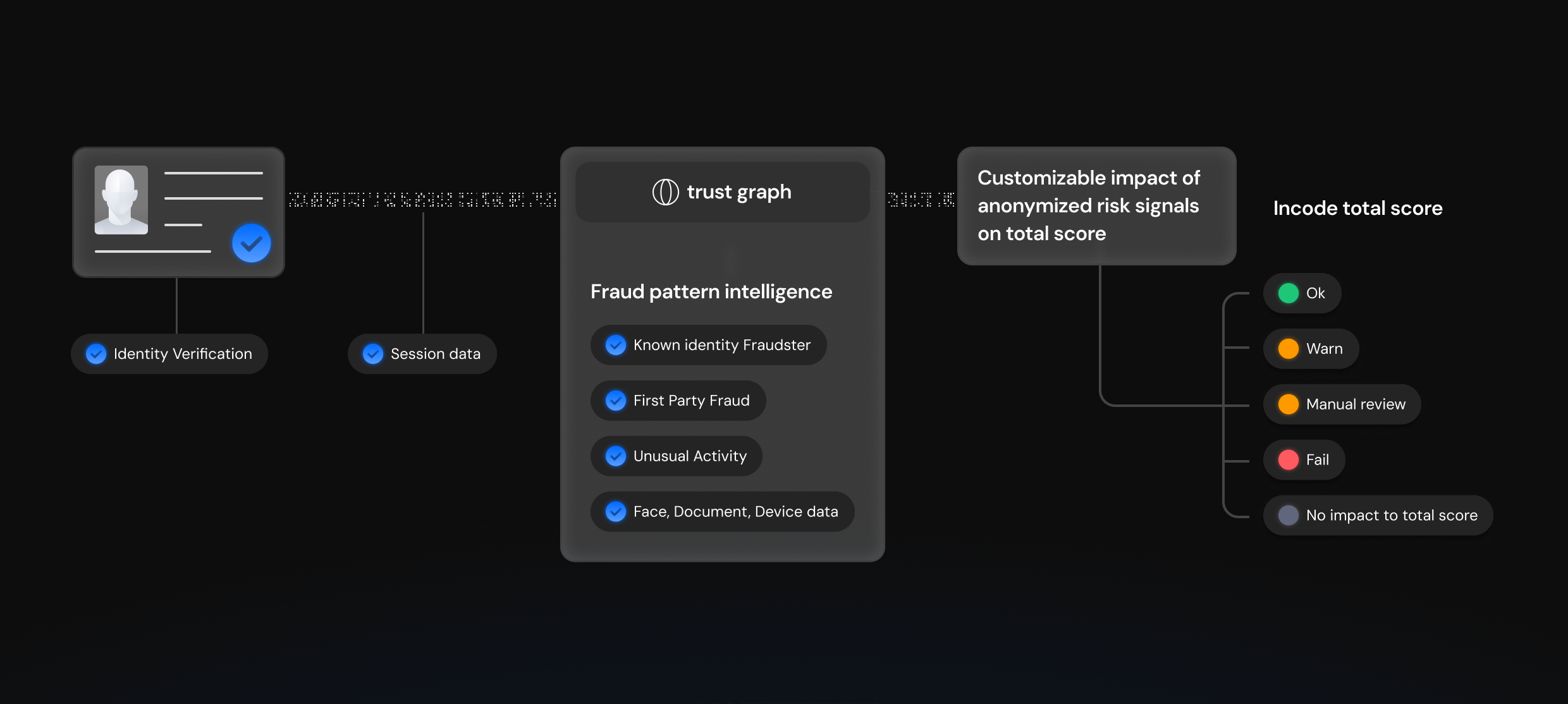



Known Fraudster Identity
Trust Graph detects when an identity, device, or document has already been confirmed as fraudulent. By recognizing repeat usage, it blocks fraudsters before they can re-enter through another customer.
First-party Fraud:
Trust Graph uncovers when legitimate users engage in fraudulent activity, such as repeated chargebacks or misuse of their accounts. These reports are shared across the network, giving clients visibility into behaviors that might otherwise go unnoticed.
Unusual Activity
Trust Graph surfaces anomalous behaviors or risk patterns that deviate from normal user activity, such as velocity spikes or inconsistent logins. These signals help highlight potential fraud even when an identity has not been previously flagged.
Frequency & Repeat Attempt
Fraudsters often reuse the same credentials, devices, or tactics across multiple attempts. Trust Graph tracks repetition and frequency, exposing suspicious patterns that single, isolated checks might miss.
Cross Organization Fraud Detection
Fraudsters move across organizations undetected
Incode’s technology gives you real-time, relationship-based scoring across a trusted network to stop repeat fraud before it impacts your business.
Comprehensive fraud intelligence
Enable fast, secure access to digital government services while reducing manual workloads.
Secure fraud risk sharing
Verify identities against authoritative government systems of record to ensure accuracy and regulatory alignment.
Continuous monitoring
Detect and block AI-powered threats such as deepfakes, injection attacks, and synthetic identities before they compromise systems.
Customizable risk rules
Protect public funds and critical infrastructure from misuse and organized fraud rings.
Detect repeat and evolving fraud
Gain stronger protection without exposing sensitive data
Global recognition
Customers and industry leaders
trust Incode
Verified reviews, certifications, and customer stories show the impact of Incode’s technology.
Incode leads G2’s Index for Identity Verification with top customer ratings

Incode’s identity verification system exceeds all expectations.
Resources
Latest resources con fraud prevention
Get in touch
Detect repeat fraud
Gain stronger protection without exposing sensitive data.

Contact Us